Having a computer incident response plan in place is crucial for any organization to effectively respond to cyber security threats and attacks. This plan outlines the steps that need to be taken in the event of a security breach, minimizing damage and ensuring a swift recovery.
By having a well-defined incident response plan, organizations can mitigate risks and protect their sensitive data from falling into the wrong hands. It is essential for businesses to have a structured approach to handling security incidents to minimize downtime and financial losses.
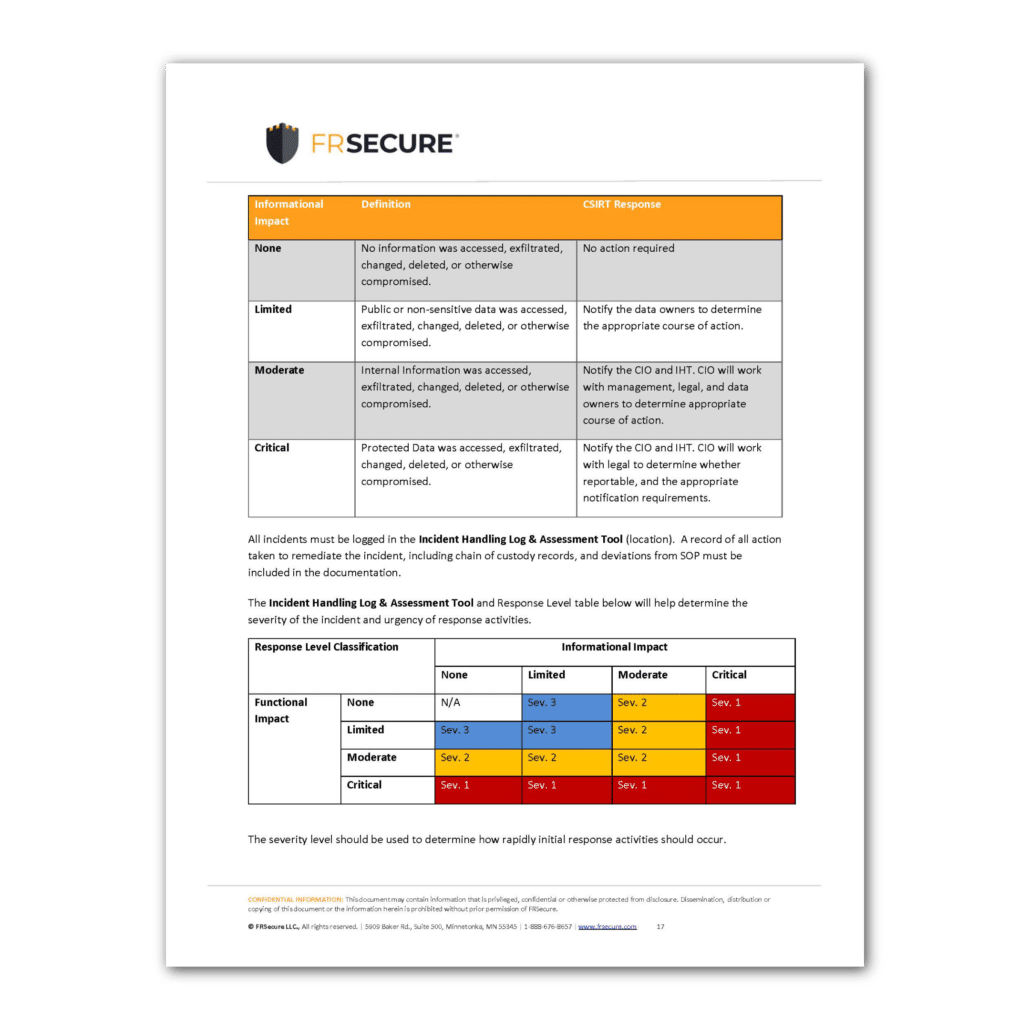
Computer Incident Response Plan Template
1. Preparation: The first step in creating an incident response plan is to identify potential risks and vulnerabilities. This includes conducting a risk assessment and defining roles and responsibilities within the organization. It is important to have a dedicated team in place to handle security incidents.
2. Detection and Analysis: In this stage, organizations need to have tools and processes in place to detect security incidents in a timely manner. This includes monitoring network traffic, analyzing logs, and implementing intrusion detection systems. Once an incident is detected, it is crucial to conduct a thorough analysis to determine the scope and impact of the breach.
3. Containment and Eradication: After identifying and analyzing the security incident, the next step is to contain the breach and prevent it from spreading further. This may involve isolating affected systems, disabling compromised accounts, and implementing patches or updates to secure vulnerabilities. The goal is to eradicate the threat and prevent any further damage.
4. Recovery and Lessons Learned: Once the security incident has been contained and eradicated, the focus shifts to restoring operations and recovering any lost data. It is important to have backups in place to minimize data loss and ensure business continuity. After the incident has been resolved, it is crucial to conduct a post-incident review to identify any weaknesses in the response plan and implement improvements for future incidents.
5. Communication and Reporting: Throughout the incident response process, clear and timely communication is essential. This includes informing stakeholders, customers, and regulatory authorities about the breach and the steps being taken to address it. Organizations must also comply with data breach notification laws and regulations by reporting the incident to the appropriate authorities.
In conclusion, having a computer incident response plan template is essential for organizations to effectively respond to security incidents and protect their data. By following a structured approach and implementing best practices, businesses can minimize the impact of security breaches and ensure a swift recovery.